Cybersecurity Consulting Services

CYBERSECURITY SOLUTIONS FOR ALL USE CASES THAT WILL SOLVE YOUR TOUGHEST SECURITY PROBLEMS
We help organizations implement suitable vendors security service edge solutions to secure access to Email, the Web, Cloud Services and Private Applications. Security service edge solutions reflect the need for organizations with hybrid workforces to apply consistent security from the cloud.
We protect your applications from cyberattacks, stops ransomware, safeguard your data, stops supply chain attacks, and secure your work-from-anywhere (WFA) workforce with a coordinated security and management solution in an integrated and automated cybersecurity platform.
How Most Companies Are Easy Target For Hackers?
The average enterprise deploys 45 cybersecurity-related tools, yet the growing number of tools hasn’t resulted in a greater ability to detect and defend against attacks. In fact, enterprises that deploy more than 50 tools ranked themselves 8 percent lower in their ability to detect threats and 7 percent lower in their defensive capabilities compared to companies deploying fewer products.
Despite the use of dozens of security products, the cybersecurity problem is never effectively solved. Cyber threats continue growing in sophistication, and the attacks keep coming. Data and privacy breaches keep happening, and the costs keep rising.
Do you ever wonder why organizations fall prey to cyberattacks despite spending millions on cybersecurity? Lack of automation and security intelligence. What are the chances of defending a digital organization when facing highly sophisticated threats today with cybersecurity techniques that rely heavily on human interactions and respond slowly? It’s probably the same as bringing a knife to a gunfight.
Traditional networking lacks awareness of content, applications, users, devices, location and more. Organizations have overlaid security solutions on to the network later to account for this shortcoming. Such overlaid security infrastructures are hard to manage, limit visibility to the true state of security, and have created gaps between silos or mismatched policies and then you breached.
Security Service Edge take the Hack out of Hackers
Provides Secure Integrated Digital Engineering Services to help organizations evolve beyond silos and point solutions to support the digital business today and in the future. Secure Access Service Edge (SASE) and Security Service Edge (SSE) optimized networking and robust security to all locations, applications, and users, regardless of where they are located. Provisioning of new resources and capabilities is fast and simple. Just deploy the right edge client and plug it into the SASE platform — pre-configured corporate policies drive the network and security experience.
Hackers methodology
The software and targets may change, but the general penetration methods do not. How hackers break in has remained mostly unchanged for decades. Hackers and their motivations may vary widely, but hacking techniques don’t substantially differ. Most hackers follow a common methodology of standard step.
Some of these have been around for decades and some are new and novel. A hacker can skip one or more of the steps and still be a successful hacker. Malware and other hacking tools often allow hackers to skip steps, but at least one of the steps, the initial penetration foothold, is always required. It is what makes a hacker a hacker. And defeating that step is crucial.
How SASE can help
One innovative approach that integrates advanced security and networking into one solution that defeats that initial penetration foothold is called secure access service edge (SASE), which allows IT teams to create a more robust, reliable, and trusted network infrastructure to operate efficiently and safely, and best serve users.
SASE redefine network security architectures
Identities are the new center for access decisions. Much like an intelligent switchboard, identities are connected to networked capabilities via the SASE vendor’s worldwide fabric of secure access capabilities. Whether we are connecting users to internal apps, cloud-based apps, SaaS, or the internet in general, these all-present variations of the same secure access problem.
A branch office is simply a place where multiple users are concentrated. Likewise, a salesperson in a car accessing Salesforce is a branch office of one. An IoT edge location is a branch office of devices. All of these are endpoint identities needing access to networked capabilities spread throughout the internet.
Advanced SASE Defense Cybersecurity Solutions:
Minimize the attack surface
Enabling applications to connect to users instead of connecting users to applications eliminates the traditional inside-outside distinction. This approach makes applications and data assets invisible to attackers while enabling users to access the right applications wherever they are while enforcing principles of least privileged access. This means making access controls adaptive, taking into account identity-based permissions and contextual factors like device type, location, and real-time threat activity when granting or preventing access.
Stops Ongoing Threat of Ransomware
Static analysis and dynamic analysis tools enable organizations to discover if there is anything suspicious about a file or if it contains any malicious code. SASE offers these capabilities as part of its IPS engine or Firewall as a Service (FaaS) functionality.
Zero Trust Network Access
Strategic Planning Implementation
Zscaler
.png)
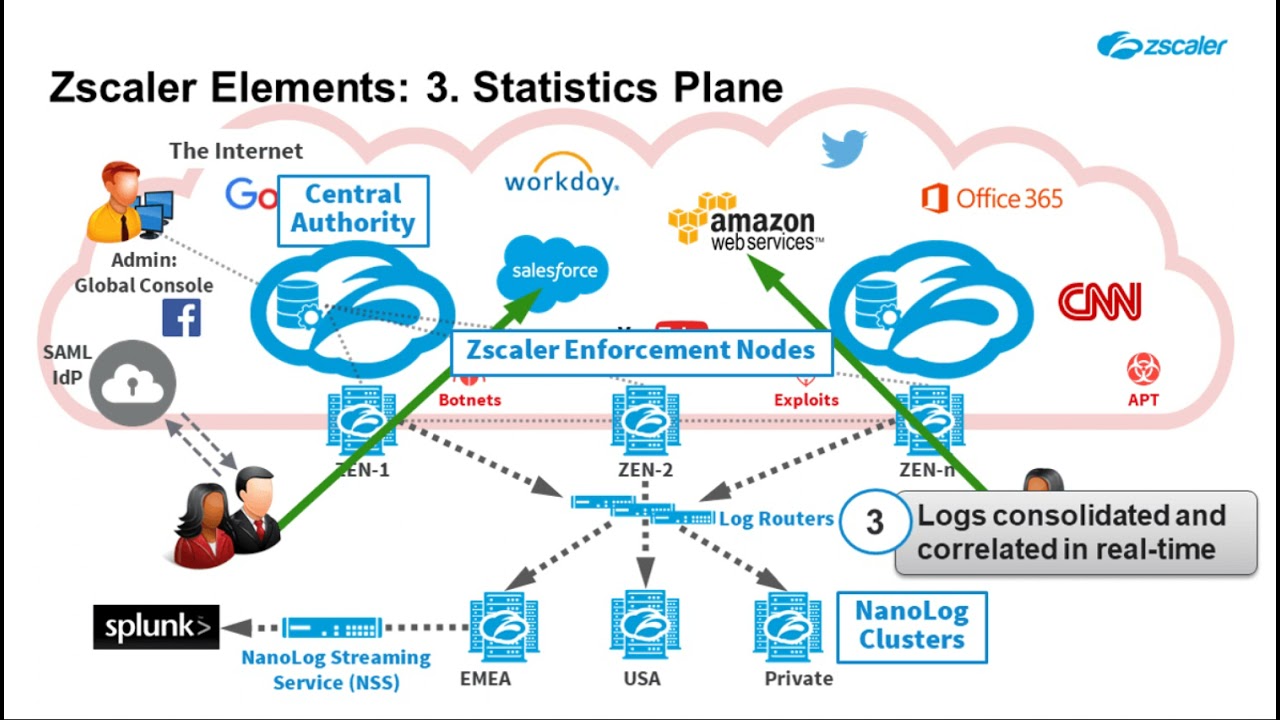
The Zscaler Cloud Security Platform is a SASE service built from the ground up for performance and scalability. As a globally distributed platform, users are always a short hop to their applications, and through peering with hundreds of partners in major internet exchanges around the world, the San Jose, Calif.-based cloud security vendor provides optimal performance and reliability for your users.
The Zscaler SASE architecture helps accelerate cloud adoption by removing network and security friction, consolidating and simplifying IT services, and eliminating the need for device management. The Zscaler platform globally peers at the edge with leading application and service providers and optimizes traffic routing to provide the best user experience.
As a fully cloud-delivered service, Zscaler provides native app segmentation by using business policies to connect an authenticated user to an authorized app without bringing the user on the network. Adversaries can’t attack what they can’t see, which is why the Zscaler architecture hides source identities by obfuscating their IP addresses and avoids exposing the corporate network to the internet.
Netskope
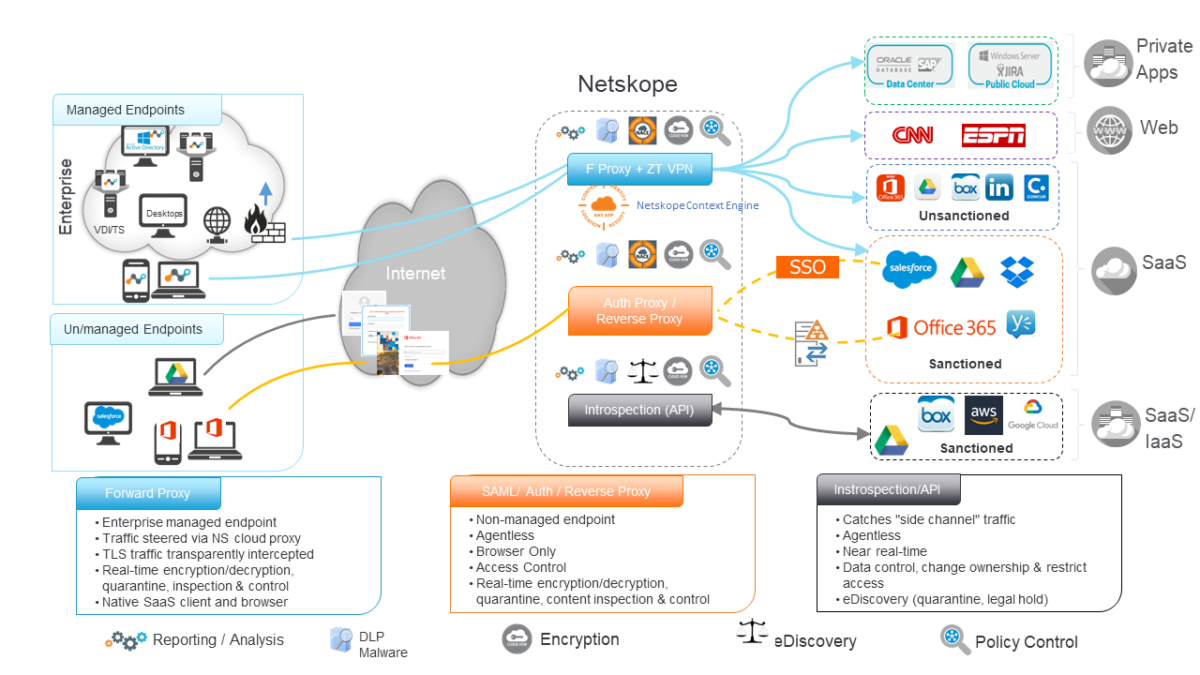
Netskope Security Service Edge (SSE) delivers advanced threat protection against cloud-enabled threats and safeguards data across any cloud, any application, or any user. The platform offers customers deep visibility across all traffic, including web and SaaS applications, cloud services, and private applications, providing granular control over activities that enable customers to secure their remote workforce.
Explicit and granular access controls across applications, application instances, and application activities reduce the attack surface against threat vectors like risky cloud apps, cloud phishing of sanctioned app credentials. Netskope incorporates deep learning models into AI/ML-based image classification for content detection of passports, government IDs, credit cards, social security cards, and other data types.
With global coverage, efficient traffic processing, low-latency on-ramps and extensive peering, the Netskope NewEdge security private cloud delivers SSE without performance trade-offs to boost productivity and business agility. With 99.999% uptime & availability plus industry-leading latency SLAs for traffic processing, customers can be confident Netskope services remain up and highly available.
Palo Alto Networks Prisma SASE
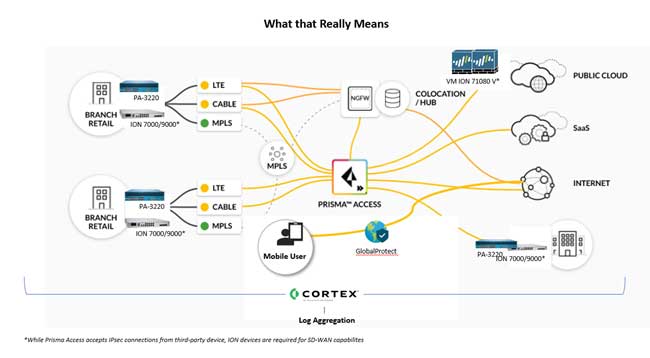
Palo Alto Networks Prisma SASE converges best-of-breed security with best-of-breed next-gen SD-WAN into a cloud-delivered platform. It consolidates multiple point products, including ZTNA, Cloud SWG, next-gen CASB, FWaaS, SD-WAN and ADEM into a single integrated service, reducing network and security complexity while increasing organizational agility.
Prisma SASE consistently secures all apps used by an organization’s hybrid workforce, regardless of whether users are remote, mobile, or working from a branch office. The Santa Clara, Calif.-based company’s proven cloud-delivered security services leverage ML-powered threat prevention to instantly stop 95% of web-based threats inline, significantly reducing the risk of a data breach.
Prisma SASE includes the industry’s only SASE-native Autonomous Digital Experience Management (ADEM) that helps ensure an exceptional experience for an organization’s end-users. With end-to-end visibility and insights across both mobile and branch users, guaranteed by performance SLAs that are 10x better than the closest competitors, a company’s employees will be happier and more productive.
How Can We Help You?
We help organizations architect, implement, manage, and advance their cybersecurity capabilities and operations from software development to deployment. Solutions includes cybersecurity with automation and intelligence leveraging cutting-edge technologies enables automated and intelligent managed detection and response, combined with security orchestration, automation and response, help detect and respond to cyberthreats such as ransomware in real time. Alone with context and risk-based authentication methods to help reduce the probability of unauthorized access to systems.
