How to address Network Security with Fortification Sciences?
Working on cybersecurity and threat intelligence, there are so many points to focus. We have to be careful so that there shouldn’t be any loop holes in intelligence which can eventually result in losing confidential information and data. We focused on the following points while making our platform.
-
Feature Engineering
-
Proactive steps on Correlation and Anomaly Detection
-
Threat Intelligence
-
Automated Learning
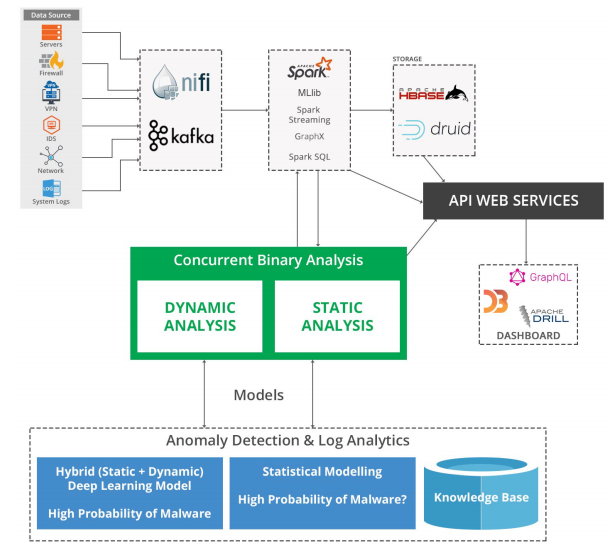
Architecture Diagram